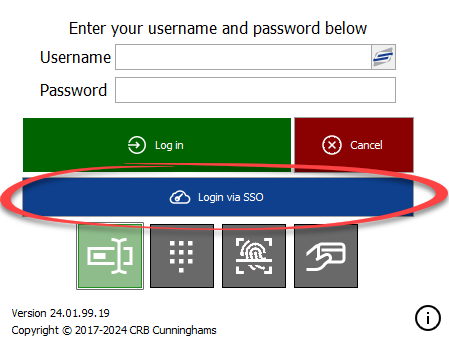
Starting with v24.1, Fusion supports the ability to access all areas of the system using Single Sign-On. When Single Sign-On has been enabled on your system, the blue ‘Login via SSO’ button will be present. Clicking this button attempts to authorise against the configured authentication service(s).
When the button is clicked, this will open up a new tab in the user’s default web browser where they will be required to authenticate against the configured authentication service. When the user is successfully authenticated, Fusion will perform one of two actions.
User logging in via SSO for the first time
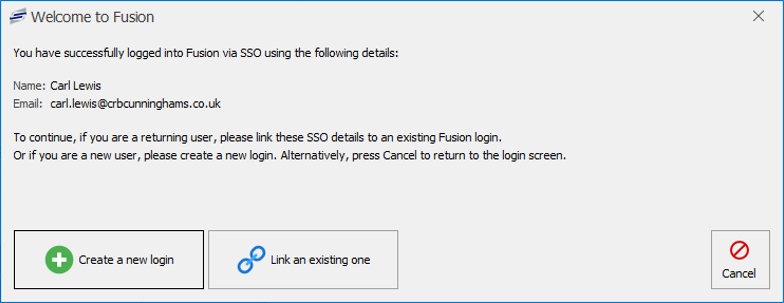
If a user has not previously logged into Fusion using SSO, when they successfully authenticate via SSO for the first time they will be presented with a ‘Welcome to Fusion’ message which will display the SSO details provided on the user’s token returned via the authentication service, prompting them if they wish to create a new login or link to an existing one.
Create a new login
If the user does not have an existing Fusion login, they should press the ‘Create a new login’ button. This will display the ‘Create new login’ prompt with the user details entered using the details on the token returned by the authentication service
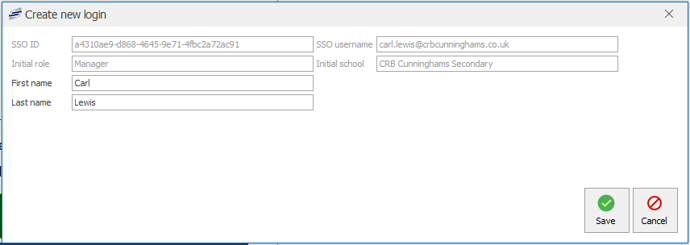
Pressing Save will create the user a new Fusion login with these details.
Link an existing one
If the user has an existing Fusion login, should elect to link these SSO details to this pre-existing login using the ‘Link an existing one’ button. Doing so will keep all the current details for that login, specifically what role(s) and School(s) the login has access to. After pressing the button, simply enter valid user credentials and press ‘Verify’. Given valid user credentials have been added (and this login has not already been linked to another SSO account) the details will be linked to this login and the user granted access.
Returning user using SSO
Finally, if a Fusion login has already been created or linked to this SSO account, then when a valid token is returned to Fusion the user is automatically logged in (assuming the login has access to log into that device, e.g. a user without the ‘Back office’ permission will not be able to log into a Back office location).


Post your comment on this topic.